In today’s digital landscape, safeguarding sensitive information and ensuring secure access to network resources has never been more critical.
Implementing effective Network Access Control Lists (ACLs) is a strategic approach that empowers organizations to control who can access their networks and under what conditions. This article delves into the top strategies for successful Network ACL implementation, providing insights into their importance, key components that should be included, and a step-by-step guide for effective execution. We will also address common challenges faced during implementation and offer solutions to overcome them, as well as the best practices for measuring the success of your access control strategies. By the end of this article, you’ll be equipped with the knowledge and tools to enhance your network security through well-structured access control measures.
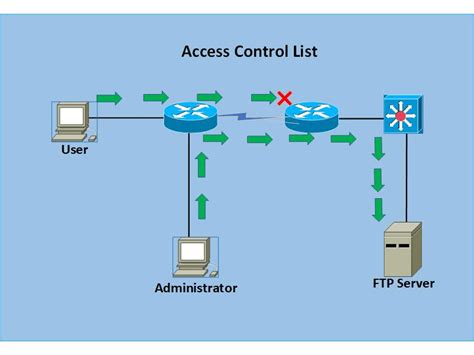
Understanding The Importance Of Network Access Control Lists
Network Access Control Lists (ACLs) play a vital role in maintaining the security and efficiency of network systems. They serve as a foundational layer for controlling traffic and ensuring that only authorized users have access to sensitive information. The implementation of strong ACLs can significantly mitigate risks associated with unauthorized access, data breaches, and other security threats.
By defining specific rules that dictate which users or devices can communicate over the network, ACLs contribute to a more manageable and secure networking environment. This structured approach helps organizations to both bolster their defense mechanisms and simplify their compliance with regulatory requirements.
Moreover, a well-designed ACL supports improved network performance by reducing unnecessary traffic. By filtering out unwanted requests, ACLs enable critical resources to function optimally, ensuring that legitimate traffic can flow smoothly. This efficiency gains importance as organizations scale and their network traffic grows.
Incorporating Top Strategies when designing ACL policies not only elevates security standards but also promotes a proactive approach to handling potential vulnerabilities. Ultimately, understanding the importance of network access control lists is crucial for any organization looking to establish a resilient cybersecurity posture and streamline their operational processes.
Key Components To Include In Your Top Strategies
When devising your Top Strategies for Network Access Control List (ACL) implementation, certain components are essential to ensure a robust framework. Here are the key elements to consider:
- Policy Definition: Clearly define access control policies that specify who can access what resources within the network. This foundational step sets the tone for the entire ACL strategy.
- Authentication Mechanisms: Implement solid authentication methods to confirm user identities before granting access. This could include multi-factor authentication (MFA) for enhanced security.
- Role-Based Access Control (RBAC): Structure permissions based on user roles to simplify management and reduce potential security risks. This approach minimizes the complexity of constantly adjusting individual user permissions.
- Network Segmentation: Divide the network into segments to control traffic flow and limit access. This strategy not only enhances security but also makes monitoring and managing network resources easier.
- Logging and Monitoring: Establish logging and continuous monitoring systems to track access attempts and changes to ACLs. This helps in quickly identifying and responding to unauthorized access efforts.
- Regular Reviews and Audits: Schedule regular reviews of your access control strategies and conduct audits to ensure compliance with established policies. This preventive measure helps identify areas that need improvement or adjustments based on evolving threats.
- User Training and Awareness: Provide training for users regarding the importance of network security and their role in maintaining it. Increased awareness can significantly reduce potential vulnerabilities.
- Integration with Security Technologies: Integrate your ACL strategies with other security tools, such as intrusion detection systems (IDS) and firewalls, to create a more comprehensive security posture.
By incorporating these key components into your Top Strategies for Network Access Control List implementation, you’ll create a more secure and efficient network environment that adapts to the ever-changing landscape of cybersecurity threats.
Step-By-Step Guide For Effective Implementation
Implementing robust network access control lists (ACLs) is crucial for enhancing your organization’s security posture. This Top Strategies guide will walk you through a clear, systematic approach to achieving effective implementation of ACLs.
Step 1: Define Network Access Requirements
Begin by evaluating and understanding the specific access requirements for various user roles, devices, and applications within your network. Documenting these requirements is critical for tailoring your access control lists effectively.
Step 2: Identify Resources and Assets
Compile a comprehensive inventory of all network resources and assets such as servers, databases, and applications. Clearly categorizing these assets enables you to determine which resources require access controls and the level of access each user or device should have.
Step 3: Develop Your ACL Policy
Create a detailed ACL policy that reflects your organization’s security objectives. The policy should outline which users or groups have access to specific resources along with defining the type of permissions (e.g., read, write, execute) that are granted.
Step 4: Implement the ACLs
With your policy in hand, you can now begin implementing the ACLs across your network devices. This may involve configuring settings on firewall devices, routers, or switches. Follow best practices for implementation to minimize the impact on network performance.
Step 5: Test and Validate
After deployment, it’s vital to rigorously test the ACLs to ensure they function as intended. Simulate various access scenarios to validate that users receive appropriate access and that unauthorized attempts are blocked.
Step 6: Monitor and Audit
Continuous monitoring is essential to ensure that your ACLs are functioning correctly over time. Regular audits will help you identify any discrepancies and evaluate whether access controls are still aligned with business needs. Use automated tools to ease the monitoring burden and ensure compliance.
Step 7: Train and Educate Users
Educating users about ACL policies and their importance is critical to compliance and security. Conduct training sessions and create easily accessible documentation to ensure that everyone understands the access controls in place and their responsibilities.
By following these steps, organizations can effectively adopt Top Strategies for implementing network access control lists, thereby strengthening their overall security posture.
Common Challenges And Solutions In Network Access Control
Implementing effective Network Access Control (NAC) strategies can present several challenges. Below are some common obstacles you may encounter, along with their respective solutions to help you navigate these issues successfully.
| Challenge | Solution |
|---|---|
| Complex Network Environments | Utilize automated tools to scan and map your network. This will help create a clear understanding of all devices and their access levels. |
| Resistance to Change from Employees | Provide comprehensive training and clear communication about the importance of NAC. Engage with employees to understand their concerns and address them directly. |
| Integration with Existing Systems | Choose NAC solutions that are compatible with your current infrastructure. Seek vendors that provide integration support. |
| Lack of Continuous Monitoring | Implement real-time monitoring tools to keep track of network traffic and access attempts continuously. Utilizing centralized logging can also aid in detecting anomalies. |
| Difficulty in Policy Management | Establish a clear policy framework before implementation, ensuring policies are regularly reviewed and updated as necessary. Use policy management software to streamline this process. |
Addressing these challenges is vital for the success of your Top Strategies in Network Access Control List implementation. By being proactive and employing the right solutions, you can create a secure and efficient network environment.
Measuring The Success Of Your Access Control Strategies
To determine the effectiveness of your access control strategies, it’s essential to establish key performance indicators (KPIs) that can provide insights into your network security posture. Utilizing these metrics, you can assess the performance of your Top Strategies for network access control lists (ACLs). Here are several methods for measuring their success:
1. Incident Response Time: Track the time it takes to respond to unauthorized access attempts. A decrease in this metric indicates that your access control measures are improving.
2. Number of Unauthorized Access Attempts: Monitor and log unauthorized access attempts. A reduction in occurrences over time suggests that your Top Strategies are effectively filtering out potential intrusions.
3. Policy Compliance Rate: Evaluate how well users adhere to the defined access policies. A high compliance rate indicates successful implementation of access control strategies.
4. Audit Trails and Logs: Regularly review audit trails and access logs to evaluate the efficiency of your ACLs. Pay attention to atypical access patterns that may indicate flaws in your current strategies.
5. User Feedback and Awareness: Conduct surveys or assessments to gauge the awareness and understanding of access policies among users. This feedback can inform you about potential areas for improvement.