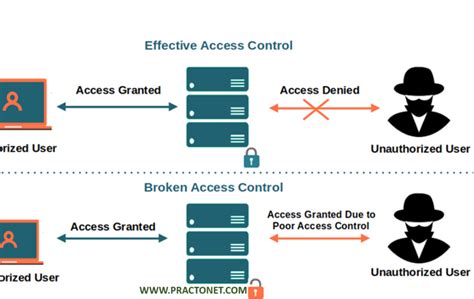
In today’s digital landscape, where data breaches and cyber threats are increasingly prevalent, understanding broken access control is imperative for safeguarding sensitive information.
This guide serves as your comprehensive resource, delving into what broken access control is and why it poses significant risks to your organization. From identifying common vulnerabilities to exploring effective prevention strategies, we will equip you with the knowledge to protect your systems. Whether you’re a seasoned security expert or just starting, this article aims to clarify the intricacies of broken access control, empowering you to effectively evaluate its impact on your security posture. Join us as we navigate through essential insights to bolster your defenses against this critical threat.
What Is Broken Access Control And Why It Matters
Broken access control refers to a security vulnerability that allows unauthorized users to gain access to restricted resources or functionalities within a system. This can occur when applications do not properly enforce access controls, allowing users to perform actions or access data they are not permitted to. As organizations increasingly rely on digital platforms to manage sensitive information, understanding and addressing broken access control is crucial to safeguarding data integrity and ensuring compliance with regulations.
There are several reasons why broken access control matters significantly:
- The Ultimate risk of unauthorized access: Weak access controls can lead to data breaches, exposing sensitive information to malicious actors.
- Compliance issues: Organizations that fail to implement adequate access controls may violate industry regulations, leading to hefty fines and legal repercussions.
- Impact on reputation: Data breaches resulting from broken access control can severely damage an organization’s reputation and erode customer trust.
- Financial implications: The costs associated with data breaches and recovery efforts can be substantial, impacting an organization’s bottom line.
Understanding broken access control is essential for any organization that aims to protect its resources and maintain a secure digital environment. By being aware of the vulnerabilities and their implications, organizations can take proactive measures to mitigate risks and enhance their overall security posture.
Common Causes of Broken Access Control Explained
Understanding the common causes of broken access control is essential for safeguarding your applications and data. Here’s an analysis of the primary reasons these vulnerabilities arise:
- Improperly Configured Access Controls: Many organizations fail to set access controls correctly, granting more permissions than necessary to users, which can lead to unauthorized actions.
- Hardcoded Access Controls: Relying on hardcoded values for checks can lead to vulnerabilities. When these checks remain static, they can be easily bypassed by attackers.
- Ambiguous Authorizations: When there is a lack of clarity about what users are authorized to do, it creates confusion and potential loopholes for unauthorized access.
- Overlooking Inheritance of Permissions: In systems employing user roles, neglecting to implement strict checks on inherited permissions can result in users gaining unintended access to sensitive data.
- Inadequate Session Management: Poor handling of user sessions can allow unauthorized users to hijack active sessions, thereby bypassing access controls.
- Insufficient Input Validation: Failing to validate user inputs can lead to injection attacks, which may exploit access control measures.
- Lack of Continuous Monitoring: Without active monitoring of user activities, it becomes difficult to detect suspicious actions or changes in access patterns that could indicate broken access control.
By addressing these common causes, organizations can significantly strengthen their defenses against broken access control, ensuring that their systems remain secure and compliant with regulations. The awareness of these factors is a crucial step in achieving the ultimate level of security for your applications.
The Ultimate Strategies to Prevent Broken Access Control
Preventing broken access control is critical for securing sensitive data and maintaining the integrity of your systems. Here are the ultimate strategies that can help organizations mitigate the risks associated with this vulnerability:
- Implement Role-Based Access Control (RBAC): Define roles within your organization and grant permissions based on these roles. This limits user access strictly to what is necessary for their job functions.
- Enforce the Principle of Least Privilege: Ensure users have the minimum level of access required to perform their duties. Regularly review and adjust these privileges to maintain security over time.
- Utilize Strong Authentication Mechanisms: Incorporate multi-factor authentication (MFA) to add an additional layer of security, making it more difficult for unauthorized users to gain access.
- Regularly Audit and Monitor Access Logs: Establish continuous monitoring of access logs to detect unusual activities promptly. Regular audits can also help uncover potential weaknesses before they are exploited.
- Conduct Security Training: Educate employees about the importance of access control and the risks associated with mismanagement. Empowering users can reduce human errors that may lead to vulnerabilities.
- Automate Permissions Management: Employ tools that help automate the management of access permissions. This ensures that access rights are consistently enforced and reduces the chances of human error.
- Regularly Test and Assess Access Control Measures: Perform penetration testing and vulnerability assessments to understand how well your controls are performing and to identify areas for improvement.
By implementing the ultimate strategies outlined above, organizations can significantly reduce the risk of broken access control and protect their sensitive data against unauthorized access.
How To Identify Broken Access Control Vulnerabilities
Identifying broken access control vulnerabilities is crucial in safeguarding your applications and data. Here are some effective techniques to help you identify such vulnerabilities:
By implementing these strategies, you’re taking a significant step towards enhancing the security of your applications and preventing broken access control vulnerabilities, which can ultimately protect your organization from various security threats. Remember, a continual assessment in line with The Ultimate security practices will ensure robust access control mechanisms are in place.
Evaluating The Impact of Broken Access Control on Security
Broken access control is a significant vulnerability that can lead to severe repercussions for organizations. To understand its impact on security, it’s essential to evaluate how these vulnerabilities can affect both the integrity of the systems and the data they manage. Here are some key areas to consider:
| Impact Area | Description |
|---|---|
| Data Breach | Unauthorized access can lead to the exposure of sensitive data, resulting in legal penalties and loss of user trust. |
| Reputation Damage | A security incident related to broken access control can tarnish an organization’s reputation, impacting customer loyalty and market position. |
| Financial Loss | Data breaches often have significant financial repercussions due to fines, litigation costs, and the expenses associated with mitigation efforts. |
| Compliance Issues | Breach of access control may lead to violations of regulations such as GDPR or HIPAA, resulting in additional fines and legal constraints. |
| Service Disruption | Exploiting access controls can lead to service outages, impacting operations and customer satisfaction. |
In essence, the impact of broken access control extends far beyond technical flaws, affecting all facets of an organization. Organizations must adopt a proactive stance towards assessing risks associated with access controls, thus reinforcing their security posture. Remember, addressing these vulnerabilities is not just about compliance; it’s ultimately about protecting your organization and its stakeholders.
In the context of The Ultimate guide to security, understanding and mitigating the impact of broken access control will ensure that organizations can safeguard their most valuable assets effectively.
Frequently Asked Questions
What is broken access control?
Broken access control refers to a security vulnerability that allows unauthorized users to gain access to restricted resources or information within an application or system.
What are common types of broken access control vulnerabilities?
Common types of broken access control vulnerabilities include horizontal privilege escalation (accessing data of other users with the same level of permissions), vertical privilege escalation (accessing data of users with higher privileges), and insecure direct object references.
How can organizations prevent broken access control?
Organizations can prevent broken access control by implementing proper authentication and authorization mechanisms, conducting regular security audits, and ensuring least privilege access policies are followed.
What role does user input validation play in preventing broken access control?
User input validation is crucial in preventing broken access control as it helps to ensure that only legitimate requests are processed, rejecting any that may seek to exploit access control weaknesses.
Are there specific frameworks to test for broken access control vulnerabilities?
Yes, numerous security frameworks and tools such as OWASP ZAP, Burp Suite, and others can be used to identify and test for broken access control vulnerabilities during security assessments.
What is the impact of broken access control on businesses?
The impact of broken access control on businesses can be significant, leading to data breaches, loss of customer trust, potential legal liabilities, and financial losses.
How often should organizations review their access control policies?
Organizations should review their access control policies regularly, ideally at least annually or after significant changes in their systems or user roles, to ensure they remain effective and secure.