Everything You Should Know About What Is Role Based Access Control Systems
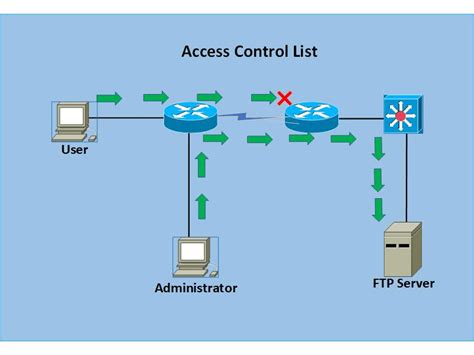
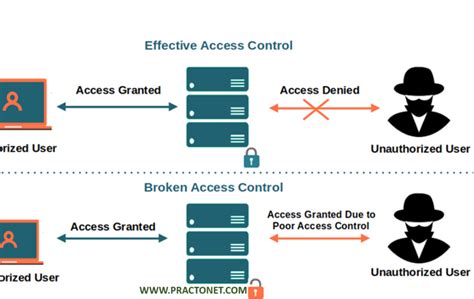
In today’s digital landscape, safeguarding sensitive information is paramount, and Role-Based Access Control (RBAC) systems play a crucial role in achieving this goal. RBAC is a strategic framework that allows organizations to manage user permissions based on their roles within the company, ensuring that individuals have access only to the data necessary for their specific … Read more